por Maria Mercedes Arechavaleta / Noviembre, 2009
El valor de la información de su empresa va más lejos de servir para su análisis. Ella tiene un valor en el mercado y por ello existen los piratas informáticos, quienes se dedican a violar la seguridad de los sistemas de las empresas con el objeto de obtener dicha información y venderla. El artículo de hoy le presenta formas concretas de proteger su información.
Continue reading this article, CLICK HERE
Saturday, November 14, 2009
Does your IT model lead or follow the competition?
by Leslie Satenstein / November, 2009
With the advent of high speed networks and the globalization of the market place, companies are being squeezed to reduce costs in order to remain competitive. As technology becomes pervasive around the globe, there has been a paradigm shift to providing low cost fast ways of delivering IT technology. The business process reengineering that is occurring is due to SaaS and to free and Open Software. This article describes the decisions that world corporations and SMBs are taking to cut IT costs in order to permit sustainable growth.
Continue reading this Article. CLICK HERE
With the advent of high speed networks and the globalization of the market place, companies are being squeezed to reduce costs in order to remain competitive. As technology becomes pervasive around the globe, there has been a paradigm shift to providing low cost fast ways of delivering IT technology. The business process reengineering that is occurring is due to SaaS and to free and Open Software. This article describes the decisions that world corporations and SMBs are taking to cut IT costs in order to permit sustainable growth.
Continue reading this Article. CLICK HERE
Sunday, October 25, 2009
The role of eCLIPse in Security
by Leslie Satenstein
October, 2009
Prior to describing Eclipse, the industry uses several terms that need some definitions.
Data In The Clear
Data that is stored so that what you see is what you get. For example, this text and the email you receive from contacts is in the clear. Anyone can read it or make use of it. Excel Spreadsheets, lawyer’s papers, auditors working papers, etc or even one’s confidential diary is normally available to anyone who receives a copy.
Encryption
Encryption is the process of taking a file of “data in the clear”, and using a mathematical algorithm such as 3DES, driven by keywords, to convert the data in such a way that it now appears as gibberish. To decrypt the data requires the use of a keyword or a second keyword. Encryption is used to provide privacy of information. A quality of modern encryption algorithms, is that someone who does not have the keyword(s) required to undo the encryption process, would normally require a lifetime of years of effort employing dozens of superfast computers, to try to restore the data to it’s original form (to break the encryption code).
Some encryption algorithms are rated very strong while others are weaker. The standard connection between computers and wireless networks use weak encryption and the encryption can be easily discovered, however, eCLIPse uses a strong encryption algorithm « Triple Des » (3DES) that is virtually impossible to break. 3DES is used in banking networks and in transmitting data between individuals. 3DES encryption is used for various tasks, including secure storage, protecting online databases and other security requirements.
How secure is 3DES ?
It seems reasonable, given that we recommend using 3DES, to ask, « Is it safe? » The answer is « It is very safe ». There is a technical description that is beyond the scope of this article, which explains that because eCLIPse imposes the use of distinct keys it can take about 2^168 (2 raised to the power 168) crypto operations to discover the 3DES key. Assuming that each 3DES decryption test requires 2 decryptions plus one encryption) at a million instructions per second, it will amount to 1.19 x 10^37 or more then 137 million years to discover the key. That's far longer than scientists currently estimate our universe to have been in existence.
SSL
Secure Socket Layer or SSL is a transmission protocol that is layered onto TPNS. It is a security to dynamically chose encryption and decryption keys, and to keep the user to partner and partner to user transmission contents fully encrypted. Eclipse fully supports SSL. A common use of SSL is securing internet website access sessions.
Virtual Private Network (VPN)
The internet is a highway that is open to all, and in particular, opens to snooping. Virtual Private Networks (VPN) uses SSL encryption to establish connections for all traffic between a remote host and a network. VPNs are typically used when remote workers connect to the office network. VPNs use secure channels to exchange data, the channel is encrypted between the remote computer and network to protect private information. However the files may not be encrypted and may be stored in the computer in the clear. Eclipse supports VPN, SSL, and allows end-to-end transfer of encrypted files, safe from problems due to illicit copy or laptop theft.
Wireless Networks
Wireless network protocols like WPA and WEP use encryption to secure communication between the router and computer. Both of these encryption algorithms are weak, allowing someone with a message analyzer, to break in and eavesdrop. Since WPA or WEP code is easily broken, it is best to use eCLIPSe to encrypt the files before transmission to the host. This use ensures that even if one can take copies of the data during wireless transmission, the data will appear as illegible characters.
File Storage Security
In transmitting or archiving encrypted files, one should have a method to keep track of the keys used to encrypt them. Lose the key and the file is lost. With eCLIPSe, a collection of keys is stored within a Smart USB Token, or, in other cases, in an eCLIPSe virtual token server in a host environment. For security purposes, the keys are not known to the users. In normal use, the user requests encryption and decryption and the software takes over, using the extracted keys from the token or from the virtual server.
While there is free compression software like WinZip that supports primitive password protection, a problem arises in the requirement to keep secret, the encryption keys used.
USB Tokens are actually computers on a chip. eCLIPSe is based on USB Tokens which store the 3DES keys. To access the keys, a logon (PIN) is required before the token contents can be fetched. The chip cannot be interrogated unless the logon code is known. Eclipse uses the “3 strikes and you are out” rule to lock up the USB token if the wrong Alphanumeric PIN (Alphanumeric Personal Identification Number) is used incorrectly 3 consecutive times. Individual files and folders can easily be encrypted using eCLIPSe.
Encrypted Hard drives
Encryption can be used to hide the contents within a computer. Entire hard drives can be encrypted using encryption software to ensure that no one can access the directory. Software like PGP and TrueCrypt are good for hard drive encryption. The disadvantage is that once the encryption key to access the hard drive is known, all the files in that drive are visible in the clear. eCLIPSe is recommended to be used to encrypt the files that are stored within an encrypted hard drive. There is also problems with creating links (shortcuts) in the encrypted partition that refers to non-encrypted directories.
Secure Socket Layer (SSL)
eCLIPse has a virtual server facility that uses and supports SSL, an encryption method used for secure Internet communication. SSL is used for shopping websites, online banking, and any other secure login or credit card processing websites. The use of SSL on websites ensures that the transferred information although capture-able, cannot be determined. eCLIPse communicates with the eCLIPse Virtual Server using SSL.
The eCLIPse API library
eCLIPse includes a full API library to manage encryption and encryption keys. Not only can the programmer implement encryption in his own applications, he can do so for sensitive database fields. Databases, known to be fully encrypted are known to be prone to security hacking to successfully bypass the built-in database security. eCLIPse provides the API so that confidential fields (credit cards, social security numbers, and other confidential data) can be fully protected. This permits simpler database setups, allowing for use of standard database backup and recovery utilities.
Wind-up
eCLIPse addresses problems that are of concern to laptop users, namely
a) the problem of maintaining data confidentiality if the laptop is stolen,
b) maintaining data confidentiality during transmission,
c) Ensuring that the data received on the target system is only visible to members in the same business group who share encryption/decryption keys,
d) other applications (database, etc.) may use eCLIPse and
e) eCLIPse use is very easy and semi-transparent for use by non computer expert “end users”.
Thanks to Alex Hankewicz contribution
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
October, 2009
Prior to describing Eclipse, the industry uses several terms that need some definitions.
Data In The Clear
Data that is stored so that what you see is what you get. For example, this text and the email you receive from contacts is in the clear. Anyone can read it or make use of it. Excel Spreadsheets, lawyer’s papers, auditors working papers, etc or even one’s confidential diary is normally available to anyone who receives a copy.
Encryption
Encryption is the process of taking a file of “data in the clear”, and using a mathematical algorithm such as 3DES, driven by keywords, to convert the data in such a way that it now appears as gibberish. To decrypt the data requires the use of a keyword or a second keyword. Encryption is used to provide privacy of information. A quality of modern encryption algorithms, is that someone who does not have the keyword(s) required to undo the encryption process, would normally require a lifetime of years of effort employing dozens of superfast computers, to try to restore the data to it’s original form (to break the encryption code).
Some encryption algorithms are rated very strong while others are weaker. The standard connection between computers and wireless networks use weak encryption and the encryption can be easily discovered, however, eCLIPse uses a strong encryption algorithm « Triple Des » (3DES) that is virtually impossible to break. 3DES is used in banking networks and in transmitting data between individuals. 3DES encryption is used for various tasks, including secure storage, protecting online databases and other security requirements.
How secure is 3DES ?
It seems reasonable, given that we recommend using 3DES, to ask, « Is it safe? » The answer is « It is very safe ». There is a technical description that is beyond the scope of this article, which explains that because eCLIPse imposes the use of distinct keys it can take about 2^168 (2 raised to the power 168) crypto operations to discover the 3DES key. Assuming that each 3DES decryption test requires 2 decryptions plus one encryption) at a million instructions per second, it will amount to 1.19 x 10^37 or more then 137 million years to discover the key. That's far longer than scientists currently estimate our universe to have been in existence.
SSL
Secure Socket Layer or SSL is a transmission protocol that is layered onto TPNS. It is a security to dynamically chose encryption and decryption keys, and to keep the user to partner and partner to user transmission contents fully encrypted. Eclipse fully supports SSL. A common use of SSL is securing internet website access sessions.
Virtual Private Network (VPN)
The internet is a highway that is open to all, and in particular, opens to snooping. Virtual Private Networks (VPN) uses SSL encryption to establish connections for all traffic between a remote host and a network. VPNs are typically used when remote workers connect to the office network. VPNs use secure channels to exchange data, the channel is encrypted between the remote computer and network to protect private information. However the files may not be encrypted and may be stored in the computer in the clear. Eclipse supports VPN, SSL, and allows end-to-end transfer of encrypted files, safe from problems due to illicit copy or laptop theft.
Wireless Networks
Wireless network protocols like WPA and WEP use encryption to secure communication between the router and computer. Both of these encryption algorithms are weak, allowing someone with a message analyzer, to break in and eavesdrop. Since WPA or WEP code is easily broken, it is best to use eCLIPSe to encrypt the files before transmission to the host. This use ensures that even if one can take copies of the data during wireless transmission, the data will appear as illegible characters.
File Storage Security
In transmitting or archiving encrypted files, one should have a method to keep track of the keys used to encrypt them. Lose the key and the file is lost. With eCLIPSe, a collection of keys is stored within a Smart USB Token, or, in other cases, in an eCLIPSe virtual token server in a host environment. For security purposes, the keys are not known to the users. In normal use, the user requests encryption and decryption and the software takes over, using the extracted keys from the token or from the virtual server.
While there is free compression software like WinZip that supports primitive password protection, a problem arises in the requirement to keep secret, the encryption keys used.
USB Tokens are actually computers on a chip. eCLIPSe is based on USB Tokens which store the 3DES keys. To access the keys, a logon (PIN) is required before the token contents can be fetched. The chip cannot be interrogated unless the logon code is known. Eclipse uses the “3 strikes and you are out” rule to lock up the USB token if the wrong Alphanumeric PIN (Alphanumeric Personal Identification Number) is used incorrectly 3 consecutive times. Individual files and folders can easily be encrypted using eCLIPSe.
Encrypted Hard drives
Encryption can be used to hide the contents within a computer. Entire hard drives can be encrypted using encryption software to ensure that no one can access the directory. Software like PGP and TrueCrypt are good for hard drive encryption. The disadvantage is that once the encryption key to access the hard drive is known, all the files in that drive are visible in the clear. eCLIPSe is recommended to be used to encrypt the files that are stored within an encrypted hard drive. There is also problems with creating links (shortcuts) in the encrypted partition that refers to non-encrypted directories.
Secure Socket Layer (SSL)
eCLIPse has a virtual server facility that uses and supports SSL, an encryption method used for secure Internet communication. SSL is used for shopping websites, online banking, and any other secure login or credit card processing websites. The use of SSL on websites ensures that the transferred information although capture-able, cannot be determined. eCLIPse communicates with the eCLIPse Virtual Server using SSL.
The eCLIPse API library
eCLIPse includes a full API library to manage encryption and encryption keys. Not only can the programmer implement encryption in his own applications, he can do so for sensitive database fields. Databases, known to be fully encrypted are known to be prone to security hacking to successfully bypass the built-in database security. eCLIPse provides the API so that confidential fields (credit cards, social security numbers, and other confidential data) can be fully protected. This permits simpler database setups, allowing for use of standard database backup and recovery utilities.
Wind-up
eCLIPse addresses problems that are of concern to laptop users, namely
a) the problem of maintaining data confidentiality if the laptop is stolen,
b) maintaining data confidentiality during transmission,
c) Ensuring that the data received on the target system is only visible to members in the same business group who share encryption/decryption keys,
d) other applications (database, etc.) may use eCLIPse and
e) eCLIPse use is very easy and semi-transparent for use by non computer expert “end users”.
Thanks to Alex Hankewicz contribution
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
Labels:
eCLIPse,
Encryption,
Security
Thursday, August 27, 2009
Does This Cloud Have a Silver Lining
by Alex Hankewicz and Leslie Satenstein
September 2009
Introduction
Cloud Computing, although widely touted as an innovative new approach, to visualize computing as a utility has changed the way computing is delivered. Computing can be seen as a utility and as such can makes the acquisition of software as a service(SaaS) and shapes the way IT hardware is designed and purchased. This document is designed to allow the reader to navigate though the concepts of cloud computing and determine how it may benefit your organization.
Cloud Computing refers to both the applications delivered as services over the Internet and the hardware and systems software in the datacenters that provide those services. The services themselves have long been referred to as Software as a Service (SaaS). The datacenter hardware and software is what we will call a Cloud. When a Cloud is made available in a pay-as-you-go manner to the general public, we call it a Public Cloud; the service being sold is Utility Computing. We use the term Private Cloud to refer to internal datacenters of a business or other organization, not made available to the general public. Thus, Cloud Computing is the sum of SaaS and Utility Computing, but does not always include Private Clouds. Private Clouds are herein defined as internal web based applications where access is possible only from within the corporations intranet, but not from outside the corporate network.
People can be users or providers of SaaS, or users or providers of Utility Computing. We focus on SaaS Providers (Cloud Users) and Cloud Providers, which have received less attention than SaaS Users.
What are the fundamental characteristics of cloud computing
From a hardware point of view, three aspects are new in Cloud Computing:
1. The ability to access a wide variety of enterprise applications which provides users solutions in a relative short time interval in a word: Speed
2. The ability to provide users to pay for only applications they need and to scale incrementally as the requirements justify further expenditure of software and IT resources. To summarize: Scalability
3. IT Professionals are permitted a greater degree of flexibility as they pay based on processor time to run the application and for the CPU memory and the amount of storage that is required to manage the application. Conclusion: Agility
4. As your computer apps run via the internet the requirement for internal hard disk space is reduced considerably by exploiting the Cloud’s ability to provide temporary disk storage.
Recent CPU and memory hardware technology developments along with new manufacturing processes has improved computer hardware costs and allow powerful computers (rackmount, blade hardware, desktops, etc) delivered with excess computing capacity. On a dedicated basis of one computer per application, the computer hardware is beyond the needs of current IT applications because only a small percentage of the CPU cycles are actually used every second, with most of the activity being database to disk input/output. With the balance of the time the computer chip is idle. The bulk of the elapsed time is spent waiting for data entry or disk activity. Virtual Systems allow the isolation and sharing of these powerful hardware configurations.
In fact, in the 1960’s, IBM introduced a mainframe system called VM. While VM was mainframe client based, it was the first major commercial implementation of virtual machines and virtual computing. More recently vendors such as Red-Hat, Novell, Ubuntu, VMware and Microsoft offer VM facilities. This avalanche to VM was started by a company called VMware. VM software as other VM systems allows the one physical computer to execute application programs that emulate itself in software. Each of these applications appears to be as a dedicated computer. These emulations allow a many to one scaling of computers to hardware and as a consequence, a many to one set of operating cost reductions. One nice feature of the emulations is that it provides real-time support of your local printer to print from the cloud provider’s application.
Internet speeds
Irrespective of cloud computing, there is a requirement for faster and faster connection speeds. Cloud computing will substantially increase the demand.
Assuming, with overheads, current low cost PC hardware supports 10/100megabit speeds and in some cases, one Gigabit speeds. While faster speeds were available as proprietary offerings, there is a pending standard for 40 and 100 Gigabit Ethernet protocols, with "Pre-standard 40 Gigabit and 100 Gigabit Ethernet products — server network interface cards, routers, switch uplinks and switches are due on the market before year-end. The pent up demand will also show up in the need for new internet cabling, capable of supporting these high speeds.
In a PDF publication, John D’Ambrosia, chair of the 802.3ba task force in the IEEE and a senior research scientist at Force10 Networks, indicates quite strongly that there is pent-up demand for 40 Gigabit and 100 Gigabit Ethernet, . D'Ambrosia says even though 40/100G Ethernet products haven't arrived yet, he's already thinking ahead to terabit Ethernet standards and products by 2015. With the forecasted demand for SaaS and other cloud computing, the general call for a higher speed will be as soon as 2010.
Benefits of VM systems
Pro’s
- Lower TCO has been touted as one of the key factors in moving to a cloud model in the companies in the SMB space as they have resource constraints in both what technologies they can deploy and in IT bring staffing to support an application.
- Cloud computing brings about improvements in Risk Management in that if one of the VM slot application is hit with a virus, that virus cannot be transferred to another VM machine. The fastest cure for the eliminating the virus is to shutdown the infected machine and start a duplicate VM machine and transfer the over the application data. While not quite as simple as doing “Poof”, with the shutdown the virus has disappeared into nowhere and hopefully, with no loss of productivity.
- Cloud Computing provides for another way to have a thin client connected to a host. The comparison with Citrix to VM is as follows: Citrix offers virtual terminals such that all Citrix terminals reside in one name space, and where the crash of one Citrix terminal may bring down all the others. In the VM environment, if a VM crashes, only that one VM crashes, and turn around time to returning it on line can be as short as ten seconds
- Access to the application in the cloud is by logon and password, in an encrypted session (https://...)
All communication between user and cloud is encrypted, and in many cases, only for recognized ranges or URLS and obligatory use of Captcha phrases to accommodate the logon screen. (Captcha phrases are those images, usually at the bottom of a web page, that ask for you to enter the letters appearing visually. Sometimes they are as simple as asking you what is the value of “10 – 3”.
Con’s
- The user may have a dropped session, which may result in an open connection waiting for a response. Generally, sessions do have idle-activity timeouts; but a session timeout may be set long, leaving a potential vulnerability.
- When a user leaves his computer on for long periods without data input. The session timeout may a) drop the transactions in process, or b) save the session for a restart. Either action will impact the database system being driven by the application.
- Of the negative aspects of cloud computing and the concerns of many SMBs is the answer to the question “Where is my data and who owns the data? Is it legal for the data to be stored offshore? Does it make financial sense?” If the internet is down, how do I continue my business? Vendors counter the fears with arguments that data stored in the cloud is inherently safer than data that inevitably ends up on scattered laptops, smart-phones, flash drives and home PCs. Internet access can be made available to the same reliability as the business connected telephone system.
- If the SMB subscribes to a SaaS such as CRM or HR, there is solely an interaction with the application. Most often, the SMB does not have the ability provided to download data. Therefore, while he may own the data, he may not be able to export it.
- Bandwidth concerns may cause difficulties in being able to move large amounts of data to and from cloud environments, given that the bandwidth from a typical corporate environment
- Privacy regulations which affect company data stored in the cloud are vague and as such with compliance and privacy concerns being increasingly vigilant this could limit cloud implementation
- Governments may stipulate that the SaaS application be open to their inspections. This right of inspection must be harmonious with all governments where the distributed application data is stored.
- Software licensing the traditional business model of software designed as a permanent installation based on a fixed number of users will no longer be valid. As in a cloud environment the number of users can change as required, this may mean SLA’s will have to be redrawn to support those issues. Organizations in the SMB space can greatly benefit from adopting the cloud model as resources constraints in terms of both budget and IT staff resources limited. Cloud computing is another way to optimize those issues..
Flexibility Cloud Computing Offers through it’s component layers
To best illustrate the advantages offered within the realm of cloud computing the box below mentions each component layer followed by a brief explanation and some examples currently in use.
The six component layers of cloud computing
- Clients
- Services
- Application
- Platform
- Storage
- Infrastructure
Client
Cloud clients generally refer to either hardware or software which requires cloud computing to run the application. Examples of this can be Mobile Phones which can access multiple on line applications i.e. Google Android, iPhone, etc. Thin client applications can be supported in a PC with Linux gOS for web browsing capabilities. Thick client is by definition: when an app can run independent of the central server.
Service
Service can include products or services that are accessed and delivered in real time over the internet. i.e. PayPal, Google Maps etc. As the licensing or setup costs for an in-house version of these services may not be cost justified, the Cloud (service bureau) type of facility fills the needed gap. There can be a mix and match of in-house and SaaS applications.
Application
A SaaS application in the cloud is a service bureau application with extra accessibility rules and connectivity. A cloud application uses the cloud in the software architecture. Generally the application does not have to be installed on the users computer as it is accessed only through the internet i.e. SaaS. Many applications are only needed for a few hours per day. On a VM machine, that application can be started and available within minutes or seconds. Typical part time SaaS applications are used for Human Capital Management (HR). Other applications such as Business Intelligence (BI), Customer Relationship Management (CRM). Applications with similar characteristics fall into this category.
Platform
Unlike service bureau applications, where the hardware was an important criteria, by utilizing a cloud platform we don’t care about the platform, we care about the functionality. The Cloud platform is a virtual machine and enhances the ability to deploy applications without the cost of managing hardware and software layers. The offerings can include an integrated solution to enable workflow design, application testing and versioning. Examples .NET, Web Application Framework, Ruby on Rails.
Storage
Cloud computing is the migration of applications, storage, and other IT resources from desktops and company data centers to massive, often scattered server farms. These server farms, operated by third-party providers, are accessible to users over the “Internet Cloud”, thus giving rise to the name.
Cloud computing Storage and archiving is a new IT service and consists of the provisioning of multiple gigabytes of disk storage. Storage will be provided in a networking "cloud" for digital content providers. Thus, a hosting service setup somewhere with a new set of SaaS applications (BI, HR, Payroll and other) will exist, available via the internet. Some of these applications rely on large quantities of storage for statistical analysis or for archival data. Other applications require smaller amounts of storage, for the company that has preferred to not to host this application. In many cases, that data will not likely to be returned to the origin business.
The plus side of cloud computing is that the “cloud” vendor can provide either or both the Virtual Machine environment and the data storage. Storage that is highly scalable and managed with newer file systems designs (LVM, Z64, Tru64) allows file sizes in petabytes (one quadrillion bytes, or 1000 terabytes (a million gigabytes)). Besides scalability, these new file system designs permit rapid recovery if ever there was a system crash. The managing of archives, restoring and performance tuning for rapid access are the responsibility of the cloud vendors. ISPs currently are the majority of the cloud computing clients but this rapidly changing as more apps are developed strictly for the cloud. This coupled with the VM machine appliance, responsibility for the management of backups, database recovery, etc, is transferred to the third party of whom the bigger players are EMC2, AMAZON, and NETAPPS. Cloud storage will continue to grow as more apps are being directed to the cloud and storage will be billed as a utility based on usage per gigabyte. Some additional players in this storage space arena for Database include (Amazon SimpleDB, Google App Engine's Big Table datastore) Network attached storage (MobileMe iDisk, Nirvanix CloudNAS) (Live Mesh Live Desktop component, MobileMe push functions) Web service (Amazon Simple Storage Service, Nirvanix SDN) Backup (Backup Direct, Iron Mountain Inc services)
Infrastructure
Cloud computing infrastructure includes:
* Virtualization and automation
* Interchangeable resources such as servers, storage and network
* Management of these resources as a single fabric
* Elastic capacity (scale up or down) to respond to business demands
* Applications (and the tools to develop them) that can truly scale up or down
* Resources delivered as a service including servers, network equipment, memory, CPU, diskspace, data center facilities,
* Dynamic scaling of infrastructure which scales up and down based on application resource needs
* Variable cost service using fixed prices per resource component
* Multiple tenants typically coexist on the same infrastructure resources
* Enterprise grade infrastructure allows mid-size companies to benefit from the aggregate compute resource pools
For the SMB office business office, generally, the infrastructure required to support cloud computing is relatively simple. It consists of a telecommunication line, modem and routers capable of supporting the number of concurrent users that will need to access the SaaS application. In most SMBs, the telecom architecture is already in place due to other business requirements. In terms of servers and software to backup and restore the data, there is no infrastructure requirement. All that data and application is in the cloud, and is the responsibility of the SaaS vendor for backup management.
A final word
The key vendors have entered the domain of cloud computing in a big way, each touting their unique approaches to this growing market. The advantages of cloud computing are widely known
- No large capital investment required
- Scalable to enterprise growth requirements
- Minimal IT in-house infrastructure required.
As our current economic picture remains challenged, more and more “C-level” executives will quickly encourage an optimization of their IT investments through the migration to the cloud computing model.
Figure 1.- Below Illustrates economic advantages of cloud computing.(Click to zoom-in)
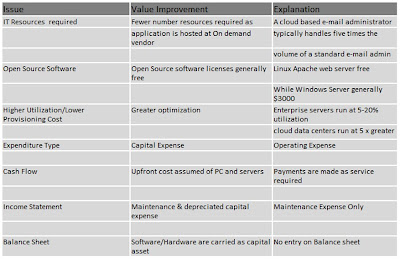
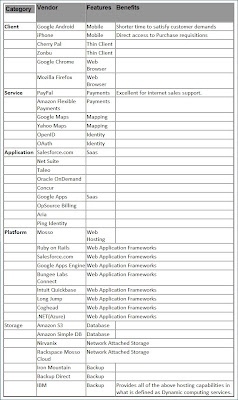
Figure 2.- Some Vendors deeply involved in Cloud Services (Click to zoom-in)
Visit itBMS web site for more details
Copyright itBMS.biz September 2009
September 2009
Introduction
Cloud Computing, although widely touted as an innovative new approach, to visualize computing as a utility has changed the way computing is delivered. Computing can be seen as a utility and as such can makes the acquisition of software as a service(SaaS) and shapes the way IT hardware is designed and purchased. This document is designed to allow the reader to navigate though the concepts of cloud computing and determine how it may benefit your organization.
Cloud Computing refers to both the applications delivered as services over the Internet and the hardware and systems software in the datacenters that provide those services. The services themselves have long been referred to as Software as a Service (SaaS). The datacenter hardware and software is what we will call a Cloud. When a Cloud is made available in a pay-as-you-go manner to the general public, we call it a Public Cloud; the service being sold is Utility Computing. We use the term Private Cloud to refer to internal datacenters of a business or other organization, not made available to the general public. Thus, Cloud Computing is the sum of SaaS and Utility Computing, but does not always include Private Clouds. Private Clouds are herein defined as internal web based applications where access is possible only from within the corporations intranet, but not from outside the corporate network.
People can be users or providers of SaaS, or users or providers of Utility Computing. We focus on SaaS Providers (Cloud Users) and Cloud Providers, which have received less attention than SaaS Users.
What are the fundamental characteristics of cloud computing
From a hardware point of view, three aspects are new in Cloud Computing:
1. The ability to access a wide variety of enterprise applications which provides users solutions in a relative short time interval in a word: Speed
2. The ability to provide users to pay for only applications they need and to scale incrementally as the requirements justify further expenditure of software and IT resources. To summarize: Scalability
3. IT Professionals are permitted a greater degree of flexibility as they pay based on processor time to run the application and for the CPU memory and the amount of storage that is required to manage the application. Conclusion: Agility
4. As your computer apps run via the internet the requirement for internal hard disk space is reduced considerably by exploiting the Cloud’s ability to provide temporary disk storage.
Recent CPU and memory hardware technology developments along with new manufacturing processes has improved computer hardware costs and allow powerful computers (rackmount, blade hardware, desktops, etc) delivered with excess computing capacity. On a dedicated basis of one computer per application, the computer hardware is beyond the needs of current IT applications because only a small percentage of the CPU cycles are actually used every second, with most of the activity being database to disk input/output. With the balance of the time the computer chip is idle. The bulk of the elapsed time is spent waiting for data entry or disk activity. Virtual Systems allow the isolation and sharing of these powerful hardware configurations.
In fact, in the 1960’s, IBM introduced a mainframe system called VM. While VM was mainframe client based, it was the first major commercial implementation of virtual machines and virtual computing. More recently vendors such as Red-Hat, Novell, Ubuntu, VMware and Microsoft offer VM facilities. This avalanche to VM was started by a company called VMware. VM software as other VM systems allows the one physical computer to execute application programs that emulate itself in software. Each of these applications appears to be as a dedicated computer. These emulations allow a many to one scaling of computers to hardware and as a consequence, a many to one set of operating cost reductions. One nice feature of the emulations is that it provides real-time support of your local printer to print from the cloud provider’s application.
Internet speeds
Irrespective of cloud computing, there is a requirement for faster and faster connection speeds. Cloud computing will substantially increase the demand.
Assuming, with overheads, current low cost PC hardware supports 10/100megabit speeds and in some cases, one Gigabit speeds. While faster speeds were available as proprietary offerings, there is a pending standard for 40 and 100 Gigabit Ethernet protocols, with "Pre-standard 40 Gigabit and 100 Gigabit Ethernet products — server network interface cards, routers, switch uplinks and switches are due on the market before year-end. The pent up demand will also show up in the need for new internet cabling, capable of supporting these high speeds.
In a PDF publication, John D’Ambrosia, chair of the 802.3ba task force in the IEEE and a senior research scientist at Force10 Networks, indicates quite strongly that there is pent-up demand for 40 Gigabit and 100 Gigabit Ethernet, . D'Ambrosia says even though 40/100G Ethernet products haven't arrived yet, he's already thinking ahead to terabit Ethernet standards and products by 2015. With the forecasted demand for SaaS and other cloud computing, the general call for a higher speed will be as soon as 2010.
Benefits of VM systems
Pro’s
- Lower TCO has been touted as one of the key factors in moving to a cloud model in the companies in the SMB space as they have resource constraints in both what technologies they can deploy and in IT bring staffing to support an application.
- Cloud computing brings about improvements in Risk Management in that if one of the VM slot application is hit with a virus, that virus cannot be transferred to another VM machine. The fastest cure for the eliminating the virus is to shutdown the infected machine and start a duplicate VM machine and transfer the over the application data. While not quite as simple as doing “Poof”, with the shutdown the virus has disappeared into nowhere and hopefully, with no loss of productivity.
- Cloud Computing provides for another way to have a thin client connected to a host. The comparison with Citrix to VM is as follows: Citrix offers virtual terminals such that all Citrix terminals reside in one name space, and where the crash of one Citrix terminal may bring down all the others. In the VM environment, if a VM crashes, only that one VM crashes, and turn around time to returning it on line can be as short as ten seconds
- Access to the application in the cloud is by logon and password, in an encrypted session (https://...)
All communication between user and cloud is encrypted, and in many cases, only for recognized ranges or URLS and obligatory use of Captcha phrases to accommodate the logon screen. (Captcha phrases are those images, usually at the bottom of a web page, that ask for you to enter the letters appearing visually. Sometimes they are as simple as asking you what is the value of “10 – 3”.
Con’s
- The user may have a dropped session, which may result in an open connection waiting for a response. Generally, sessions do have idle-activity timeouts; but a session timeout may be set long, leaving a potential vulnerability.
- When a user leaves his computer on for long periods without data input. The session timeout may a) drop the transactions in process, or b) save the session for a restart. Either action will impact the database system being driven by the application.
- Of the negative aspects of cloud computing and the concerns of many SMBs is the answer to the question “Where is my data and who owns the data? Is it legal for the data to be stored offshore? Does it make financial sense?” If the internet is down, how do I continue my business? Vendors counter the fears with arguments that data stored in the cloud is inherently safer than data that inevitably ends up on scattered laptops, smart-phones, flash drives and home PCs. Internet access can be made available to the same reliability as the business connected telephone system.
- If the SMB subscribes to a SaaS such as CRM or HR, there is solely an interaction with the application. Most often, the SMB does not have the ability provided to download data. Therefore, while he may own the data, he may not be able to export it.
- Bandwidth concerns may cause difficulties in being able to move large amounts of data to and from cloud environments, given that the bandwidth from a typical corporate environment
- Privacy regulations which affect company data stored in the cloud are vague and as such with compliance and privacy concerns being increasingly vigilant this could limit cloud implementation
- Governments may stipulate that the SaaS application be open to their inspections. This right of inspection must be harmonious with all governments where the distributed application data is stored.
- Software licensing the traditional business model of software designed as a permanent installation based on a fixed number of users will no longer be valid. As in a cloud environment the number of users can change as required, this may mean SLA’s will have to be redrawn to support those issues. Organizations in the SMB space can greatly benefit from adopting the cloud model as resources constraints in terms of both budget and IT staff resources limited. Cloud computing is another way to optimize those issues..
Flexibility Cloud Computing Offers through it’s component layers
To best illustrate the advantages offered within the realm of cloud computing the box below mentions each component layer followed by a brief explanation and some examples currently in use.
The six component layers of cloud computing
- Clients
- Services
- Application
- Platform
- Storage
- Infrastructure
Client
Cloud clients generally refer to either hardware or software which requires cloud computing to run the application. Examples of this can be Mobile Phones which can access multiple on line applications i.e. Google Android, iPhone, etc. Thin client applications can be supported in a PC with Linux gOS for web browsing capabilities. Thick client is by definition: when an app can run independent of the central server.
Service
Service can include products or services that are accessed and delivered in real time over the internet. i.e. PayPal, Google Maps etc. As the licensing or setup costs for an in-house version of these services may not be cost justified, the Cloud (service bureau) type of facility fills the needed gap. There can be a mix and match of in-house and SaaS applications.
Application
A SaaS application in the cloud is a service bureau application with extra accessibility rules and connectivity. A cloud application uses the cloud in the software architecture. Generally the application does not have to be installed on the users computer as it is accessed only through the internet i.e. SaaS. Many applications are only needed for a few hours per day. On a VM machine, that application can be started and available within minutes or seconds. Typical part time SaaS applications are used for Human Capital Management (HR). Other applications such as Business Intelligence (BI), Customer Relationship Management (CRM). Applications with similar characteristics fall into this category.
Platform
Unlike service bureau applications, where the hardware was an important criteria, by utilizing a cloud platform we don’t care about the platform, we care about the functionality. The Cloud platform is a virtual machine and enhances the ability to deploy applications without the cost of managing hardware and software layers. The offerings can include an integrated solution to enable workflow design, application testing and versioning. Examples .NET, Web Application Framework, Ruby on Rails.
Storage
Cloud computing is the migration of applications, storage, and other IT resources from desktops and company data centers to massive, often scattered server farms. These server farms, operated by third-party providers, are accessible to users over the “Internet Cloud”, thus giving rise to the name.
Cloud computing Storage and archiving is a new IT service and consists of the provisioning of multiple gigabytes of disk storage. Storage will be provided in a networking "cloud" for digital content providers. Thus, a hosting service setup somewhere with a new set of SaaS applications (BI, HR, Payroll and other) will exist, available via the internet. Some of these applications rely on large quantities of storage for statistical analysis or for archival data. Other applications require smaller amounts of storage, for the company that has preferred to not to host this application. In many cases, that data will not likely to be returned to the origin business.
The plus side of cloud computing is that the “cloud” vendor can provide either or both the Virtual Machine environment and the data storage. Storage that is highly scalable and managed with newer file systems designs (LVM, Z64, Tru64) allows file sizes in petabytes (one quadrillion bytes, or 1000 terabytes (a million gigabytes)). Besides scalability, these new file system designs permit rapid recovery if ever there was a system crash. The managing of archives, restoring and performance tuning for rapid access are the responsibility of the cloud vendors. ISPs currently are the majority of the cloud computing clients but this rapidly changing as more apps are developed strictly for the cloud. This coupled with the VM machine appliance, responsibility for the management of backups, database recovery, etc, is transferred to the third party of whom the bigger players are EMC2, AMAZON, and NETAPPS. Cloud storage will continue to grow as more apps are being directed to the cloud and storage will be billed as a utility based on usage per gigabyte. Some additional players in this storage space arena for Database include (Amazon SimpleDB, Google App Engine's Big Table datastore) Network attached storage (MobileMe iDisk, Nirvanix CloudNAS) (Live Mesh Live Desktop component, MobileMe push functions) Web service (Amazon Simple Storage Service, Nirvanix SDN) Backup (Backup Direct, Iron Mountain Inc services)
Infrastructure
Cloud computing infrastructure includes:
* Virtualization and automation
* Interchangeable resources such as servers, storage and network
* Management of these resources as a single fabric
* Elastic capacity (scale up or down) to respond to business demands
* Applications (and the tools to develop them) that can truly scale up or down
* Resources delivered as a service including servers, network equipment, memory, CPU, diskspace, data center facilities,
* Dynamic scaling of infrastructure which scales up and down based on application resource needs
* Variable cost service using fixed prices per resource component
* Multiple tenants typically coexist on the same infrastructure resources
* Enterprise grade infrastructure allows mid-size companies to benefit from the aggregate compute resource pools
For the SMB office business office, generally, the infrastructure required to support cloud computing is relatively simple. It consists of a telecommunication line, modem and routers capable of supporting the number of concurrent users that will need to access the SaaS application. In most SMBs, the telecom architecture is already in place due to other business requirements. In terms of servers and software to backup and restore the data, there is no infrastructure requirement. All that data and application is in the cloud, and is the responsibility of the SaaS vendor for backup management.
A final word
The key vendors have entered the domain of cloud computing in a big way, each touting their unique approaches to this growing market. The advantages of cloud computing are widely known
- No large capital investment required
- Scalable to enterprise growth requirements
- Minimal IT in-house infrastructure required.
As our current economic picture remains challenged, more and more “C-level” executives will quickly encourage an optimization of their IT investments through the migration to the cloud computing model.
Figure 1.- Below Illustrates economic advantages of cloud computing.(Click to zoom-in)

Figure 2.- Some Vendors deeply involved in Cloud Services (Click to zoom-in)

Visit itBMS web site for more details
Copyright itBMS.biz September 2009
Wednesday, August 5, 2009
Supply Chain Management and Industry Best Practices
Leslie Satenstein / August 2009
What is a supply chain?
If your company builds a product for customers using parts purchased from suppliers, then in simplest terms you have a supply chain. A supply chain is the management of the links or nodes from various suppliers (vendors) to your customers. A supply chain therefore includes activities of CRM purchasing, logistics, warehouse management, finance, e-commerce and depending upon the industry, a lot more.
Before the advent of global communications and the internet, management best practices Supply chain was in it’s infancy and consisted mainly of knowing the lead times for delivery of products. Order management was by fax, delivery schedules uncertain, necessitating extra safety supplies to eliminate stock-outs. Today technology with high speed communication and globalization places greater importance on supply chain management. Supply chain management addresses the management of all the links/nodes and business concerns from the small manufacturer or reseller to the behemoth sized company with its multiple global distribution centers.
What is considered Best Practices
“To reduce costs and maintain customer satisfaction, most companies institute optimization exercises that lead to the best way to manage the links. Most of the time optimization activities deliver results within that enterprise. Too often, the activities of vendors and customers are not included in the optimization exercise. If a process is common across businesses generally, it would seem there is an opportunity for Best Practices” where all participants profit from optimization.
What are the elements that make up “Best Practices.”
Best Practices are the activities to ensure that the supply chain is operating as efficiently as possible and generating the highest level of customer satisfaction at the lowest cost. Best practices dictate that “Supply Chain Management” attacks three universal generalized business activities consisting of: strategic; operational; and tactical.
Strategic: This common business activity looks for opportunities to reduce costs while optimizing supplier and customer transportation delivery costs and lead-times. The strategic decisions take into account factors such as the size and location of manufacturing sites, long term supplier agreements, products to be sold and sales markets.
Operational: Every day decisions are made that affect how the products move along the supply chain links. Currently the weakest links in the supply chain process are vendors. Schedule changes to production are made due to vendor’s late deliveries, or parts problems, misunderstanding of purchasing agreements with suppliers, order changes or additions from customers and not the least, warehouse product movements. Delays are cumulative.
Tactical: Decisions focus on implementing measures that will reduce costs. Examples include best manufacturing practices, developing a purchasing strategy with favored suppliers, working with logistics companies to develop cost effective transportation and implementing warehouse strategies to reduce the cost of storing and handling inventory. Newer technologies that complement bar coding include RFID tags for pallets, boxes and items, tight links to website e-commerce systems, employing Business Intelligence (BI) software for in-depth analysis of the nodes in the supply chain activities.
What are some of the concerns?
In every industry, a “Best Practice” is developed by a group of experts who share their knowledge and experience. They work to define the best method of operating a common process. For example, the consumer goods to retail industry pulled together under ECR. ECR or “Efficient Consumer Response” is a joint trade and industry body working towards making the grocery sector as a whole more responsive to consumer demand and promote the removal of unnecessary costs from the supply chain. The Global Commerce Initiative is there to develop and publish Industry Best Practices for common processes.
If a company expects to achieve benefits from their supply chain management process, they will require some level of investment in technology.
In the Best Practices area, two flaws that cause less then optimal “Best Practice” results are shrinkage and fraud. These two elements require due diligence and close scrutiny of new and even long term vendors to detect reasons for causing cost overruns and reducing “Best Practices” benefits.
ITMBS – How can we help?
What is a supply chain?
If your company builds a product for customers using parts purchased from suppliers, then in simplest terms you have a supply chain. A supply chain is the management of the links or nodes from various suppliers (vendors) to your customers. A supply chain therefore includes activities of CRM purchasing, logistics, warehouse management, finance, e-commerce and depending upon the industry, a lot more.
Before the advent of global communications and the internet, management best practices Supply chain was in it’s infancy and consisted mainly of knowing the lead times for delivery of products. Order management was by fax, delivery schedules uncertain, necessitating extra safety supplies to eliminate stock-outs. Today technology with high speed communication and globalization places greater importance on supply chain management. Supply chain management addresses the management of all the links/nodes and business concerns from the small manufacturer or reseller to the behemoth sized company with its multiple global distribution centers.
What is considered Best Practices
“To reduce costs and maintain customer satisfaction, most companies institute optimization exercises that lead to the best way to manage the links. Most of the time optimization activities deliver results within that enterprise. Too often, the activities of vendors and customers are not included in the optimization exercise. If a process is common across businesses generally, it would seem there is an opportunity for Best Practices” where all participants profit from optimization.
What are the elements that make up “Best Practices.”
Best Practices are the activities to ensure that the supply chain is operating as efficiently as possible and generating the highest level of customer satisfaction at the lowest cost. Best practices dictate that “Supply Chain Management” attacks three universal generalized business activities consisting of: strategic; operational; and tactical.
Strategic: This common business activity looks for opportunities to reduce costs while optimizing supplier and customer transportation delivery costs and lead-times. The strategic decisions take into account factors such as the size and location of manufacturing sites, long term supplier agreements, products to be sold and sales markets.
Operational: Every day decisions are made that affect how the products move along the supply chain links. Currently the weakest links in the supply chain process are vendors. Schedule changes to production are made due to vendor’s late deliveries, or parts problems, misunderstanding of purchasing agreements with suppliers, order changes or additions from customers and not the least, warehouse product movements. Delays are cumulative.
Tactical: Decisions focus on implementing measures that will reduce costs. Examples include best manufacturing practices, developing a purchasing strategy with favored suppliers, working with logistics companies to develop cost effective transportation and implementing warehouse strategies to reduce the cost of storing and handling inventory. Newer technologies that complement bar coding include RFID tags for pallets, boxes and items, tight links to website e-commerce systems, employing Business Intelligence (BI) software for in-depth analysis of the nodes in the supply chain activities.
What are some of the concerns?
In every industry, a “Best Practice” is developed by a group of experts who share their knowledge and experience. They work to define the best method of operating a common process. For example, the consumer goods to retail industry pulled together under ECR. ECR or “Efficient Consumer Response” is a joint trade and industry body working towards making the grocery sector as a whole more responsive to consumer demand and promote the removal of unnecessary costs from the supply chain. The Global Commerce Initiative is there to develop and publish Industry Best Practices for common processes.
If a company expects to achieve benefits from their supply chain management process, they will require some level of investment in technology.
In the Best Practices area, two flaws that cause less then optimal “Best Practice” results are shrinkage and fraud. These two elements require due diligence and close scrutiny of new and even long term vendors to detect reasons for causing cost overruns and reducing “Best Practices” benefits.
ITMBS – How can we help?
ITBMS consultants have distribution and manufacturing experience in the field of supply chain and business practice optimization. ITBMS can work with you to improve existing business practices with your ERP system or to help you select a new ERP system that responds to your business requirements. Our skills include helping you adopt Internet technologies such RFID, warehouse layout and e-commerce web software.
See other articles here
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
See other articles here
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
Labels:
Best Practices,
Supply Chain Management
Wednesday, July 29, 2009
Why go ERP ? A Baker’s dozen questions to ask before you buy an ERP solution
Leslie Satenstein / July, 2009
Your business volume has grown, and your customers complain that there are too many errors in shipping quantities or wrong products, many errors in your sales invoices. Your accounting staff is complaining, the aged analysis report is showing too many overdue accounts, or accounts over the credit limits. Inventory Management seems to have misplaced goods and payables don’t seem to correspond to receipts or bin cycle counts. The supporting paperwork for must adhered to industry regulations can’t easily be matched to inventory or shipments.
The current year end financial statement makes you nervous, as numbers from your different application systems do not match. A yearly full company audit is costly because you have different systems for sales, purchasing, inventory management, and finance. You also want to do some e-commerce and are concerned about how it can be handled with your current organization. You may want to analyze sales by geographic region, by market and to generally slice and dice your analysis according to your requirements.
ERP to “The rescue”
Your business advisor recommends that you need to implement an Enterprise Resource Planning (ERP) system. You are told that the ERP system will integrate sales, purchasing, distribution, warehousing, manufacturing, ecommerce and Finance, and it will help to reduce overdue accounts, prevent overstock and dead inventory, help with finance and most of all, provide consistent financial figures for the government and auditors.
Moreover, your potential ERP system will provide business intelligence (BI) statistics about customers, product sales, and more. It can generate enough reports and information to overwhelm each manager.
You are convinced you need an ERP system but buying one, you have a few concerns about the best one, and also if your staff are going to be supportive.
Here are a Baker’s dozen questions to ask before embarking on an ERP solution!
MOST IMPORTANTLY, the following points are ones to have answers to before you make that commitment.
1.- Do you do an in-house install of the ERP system, with the necessary hardware additions and wiring?
2.- Do you choose the ERP system and outsource the hardware operation of the ERP system? (This mode allows for on-call support of the hardware, software and remote troubleshooting.)
3.- Do you search for a Software as a Service (SaaS) product and license its use? Everything is now in the hands of a provider whose system is somewhere in the world and your business is hosted therein?
4.- Have you looked at Open Source ERP software as a possibility, as well as closed source Software Vendors? There are cost advantages to the former and often, functional advantages too.
5.- Have you created a detailed Request for Quotation (RFQ) to submit to Vendors? This RFQ would be emailed to the vendors that could provide the needed solution. The RFQ would contain a list of specific business problems you need to solve, will include new features to allow for continued growth (for example, e-commerce, multi-currency, multi-warehouse, multi-company, and even new government requirements, business intelligence, statistical reporting for product trends, etc.) As an aside, in a medium sized organization, a good ERP system allows for a significant reduction in overstocked inventory, reduced stock-outs, and lower warehousing carrying costs for insurance, heating, rental, etc. After the replies, are you going to ask for a demonstration to verify the vendor claims?
6.- Are your managers volunteering to create the Key Performance Indicators (KPI)? These include managers and their staff, who need to own the new system and the accounting firm who needs to know how to use the system to conduct an audit. Are they aware that in owning the new system, the will decide which business processes are included in the ERP package, they will understand how to phase in the rollout and how to measure success with the implementation?
7.- Does your new system require application customizations, because your product is different from the norm?
8.- Are you aware of the conversion effort and costs, which include training, running the new system in test mode for a few days, and the go-live experience.
9.- If you decide to not implement the new system, you need not read further.
Completing the baker’s dozen concerns to consider before you select the vendor
10.- Can the implementation be performed in stages, as a phased approach? If the target system has modules that are nice to have, instead of essential, can you purchase the system without them and then add modules later, without undo penalties.
11.- Which managers should be involved in each implementation phase ?
12.- Do you have a good project manager, or is the vendor providing one? Oftentimes the vendor’s in-house project manager has the in-depth knowledge of the product and previous experience in its implementation. He will work with your staff to implement the system as smoothly and as cost effectively as possible. (For a single site ERP using no foreign currencies, for the implementation estimate the larger of 500 hours or the vendor’s time estimate). Review the project plan to see if it includes training, holidays, and sufficient milestones to allow biweekly tracking at first and weekly tracking as go live approaches.
Some technical considerations
13.- We hear of Service Oriented Architecture (SoA). What does this mean to you? SoA is a software system design where each module in the application is a component. There is a sales module, a finance module, etc. SoA presents the idea that we treat each module as a black box, as we would a microwave oven or a car. We don’t want to know the inner workings, but we want to use the defined interfaces (on-off and other buttons). SoA is a great concept, but thus far, it only works best or at all when all the products are supplied by a single vendor. That is, you cannot easily integrate vendor abc’s sales package with vendor def’s finance package.
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
Your business volume has grown, and your customers complain that there are too many errors in shipping quantities or wrong products, many errors in your sales invoices. Your accounting staff is complaining, the aged analysis report is showing too many overdue accounts, or accounts over the credit limits. Inventory Management seems to have misplaced goods and payables don’t seem to correspond to receipts or bin cycle counts. The supporting paperwork for must adhered to industry regulations can’t easily be matched to inventory or shipments.
The current year end financial statement makes you nervous, as numbers from your different application systems do not match. A yearly full company audit is costly because you have different systems for sales, purchasing, inventory management, and finance. You also want to do some e-commerce and are concerned about how it can be handled with your current organization. You may want to analyze sales by geographic region, by market and to generally slice and dice your analysis according to your requirements.
ERP to “The rescue”
Your business advisor recommends that you need to implement an Enterprise Resource Planning (ERP) system. You are told that the ERP system will integrate sales, purchasing, distribution, warehousing, manufacturing, ecommerce and Finance, and it will help to reduce overdue accounts, prevent overstock and dead inventory, help with finance and most of all, provide consistent financial figures for the government and auditors.
Moreover, your potential ERP system will provide business intelligence (BI) statistics about customers, product sales, and more. It can generate enough reports and information to overwhelm each manager.
You are convinced you need an ERP system but buying one, you have a few concerns about the best one, and also if your staff are going to be supportive.
Here are a Baker’s dozen questions to ask before embarking on an ERP solution!
MOST IMPORTANTLY, the following points are ones to have answers to before you make that commitment.
1.- Do you do an in-house install of the ERP system, with the necessary hardware additions and wiring?
2.- Do you choose the ERP system and outsource the hardware operation of the ERP system? (This mode allows for on-call support of the hardware, software and remote troubleshooting.)
3.- Do you search for a Software as a Service (SaaS) product and license its use? Everything is now in the hands of a provider whose system is somewhere in the world and your business is hosted therein?
4.- Have you looked at Open Source ERP software as a possibility, as well as closed source Software Vendors? There are cost advantages to the former and often, functional advantages too.
5.- Have you created a detailed Request for Quotation (RFQ) to submit to Vendors? This RFQ would be emailed to the vendors that could provide the needed solution. The RFQ would contain a list of specific business problems you need to solve, will include new features to allow for continued growth (for example, e-commerce, multi-currency, multi-warehouse, multi-company, and even new government requirements, business intelligence, statistical reporting for product trends, etc.) As an aside, in a medium sized organization, a good ERP system allows for a significant reduction in overstocked inventory, reduced stock-outs, and lower warehousing carrying costs for insurance, heating, rental, etc. After the replies, are you going to ask for a demonstration to verify the vendor claims?
6.- Are your managers volunteering to create the Key Performance Indicators (KPI)? These include managers and their staff, who need to own the new system and the accounting firm who needs to know how to use the system to conduct an audit. Are they aware that in owning the new system, the will decide which business processes are included in the ERP package, they will understand how to phase in the rollout and how to measure success with the implementation?
7.- Does your new system require application customizations, because your product is different from the norm?
8.- Are you aware of the conversion effort and costs, which include training, running the new system in test mode for a few days, and the go-live experience.
9.- If you decide to not implement the new system, you need not read further.
Completing the baker’s dozen concerns to consider before you select the vendor
10.- Can the implementation be performed in stages, as a phased approach? If the target system has modules that are nice to have, instead of essential, can you purchase the system without them and then add modules later, without undo penalties.
11.- Which managers should be involved in each implementation phase ?
12.- Do you have a good project manager, or is the vendor providing one? Oftentimes the vendor’s in-house project manager has the in-depth knowledge of the product and previous experience in its implementation. He will work with your staff to implement the system as smoothly and as cost effectively as possible. (For a single site ERP using no foreign currencies, for the implementation estimate the larger of 500 hours or the vendor’s time estimate). Review the project plan to see if it includes training, holidays, and sufficient milestones to allow biweekly tracking at first and weekly tracking as go live approaches.
Some technical considerations
13.- We hear of Service Oriented Architecture (SoA). What does this mean to you? SoA is a software system design where each module in the application is a component. There is a sales module, a finance module, etc. SoA presents the idea that we treat each module as a black box, as we would a microwave oven or a car. We don’t want to know the inner workings, but we want to use the defined interfaces (on-off and other buttons). SoA is a great concept, but thus far, it only works best or at all when all the products are supplied by a single vendor. That is, you cannot easily integrate vendor abc’s sales package with vendor def’s finance package.
Copyright 2009 itBMS - Business and Marketing Solutions Inc.
Monday, July 13, 2009
eCLIPse – Enterprise Clip Security
eCLIPse – Enterprise CLIP Security is a software security solution for any business that requires frequent exchange of secure encrypted data. eCLIPse, simple to integrate and apply, provides safe transfer of confidential data to and from authorized external resources all the while preventing unauthorized viewing. Security is managed by smart-card technology (smart-card chip fitted into a USB token). Using simple, effective and affordable physically secure USB tokens, eCLIPse functions at the National Institute of Standards ( USA’s NIST) “FIPS 140-1 level 3”)
Initialization - Setting up the keys
A standard practice is to have groups of two users from two business areas with each user only providing one half of an encryption key. The company is protected, since this practice ensures that one user does not know the other’s key choice. Putting the two halves together by random selection means that each user does not know a final key value. eCLIPse supports multiple encryption tables with randomly assigned keys. Head office security administration sets up the USB token contents to match. There are two levels of head office control. One is constructing one more tables by choosing ten keys to insert into a table, and the other is choosing which of the keys from within an assigned table will be further assigned to an individual or group. Essentially, each business area may set up its own table and assign users to specific keys.
Comparison with Hard drive Encryption
eCLIPse encryption management is the best solution. Here is why. The argument that one will provide is, why not use a hard drive that is fully encrypted, who needs eCLIPse ?
When the hard drive is encrypted, a problem may arise if a file has to be copied or if maintenance has to be performed. An encrypted copy from that hard drive may not decrypt correctly on the target device. This is usually due to hardware differences between disk drives from the same manufacturer and especially if the target drive has no encryption. If a technician has to repair the contents of the system with the encrypted hard drive, he needs the encryption / decryption keys (provided at logon). If he can log onto the system, he has access to the data, and likewise, so can a hacker. Other concerns include alpha-numeric sorting of encrypted data. There is no guarantee that in using an encrypted drive, data can be sorted in lexicographical order.
Your company’s “Information” is more valuable than the computer it is on. If your laptop computer is lost or stolen, your confidential information cannot be decrypted without your authorized USB token.
Other Uses for eCLIPse
Do you have trouble remembering all your passwords and other personal information? With eCLIPse, you can safely store them in an encrypted file protected by the USB token.
How Eclipse works
Easy, first you will receive the pre-encrypted file (s) from Head Office. The encrypted file was created choosing two of the 10 keys. Instead of transmitting the keys, the index entries of these two keys prefix the data along with other meta data, such as the encryption algorithm used. The file is sent to the user(s) using a safe file transfer method (Secure FTP in an SSH environment). Note that the 10 keys stored in the USB token are identically stored in the head office image of the token’s table.
To view the file, start eCLIPse and plug in and log-into USB token. The two key indexes and the encryption method is read from the file. The two index values are used to retrieve the decryption keys from the USB token. Along with the algorithm ID, decryption takes place. Encryption publication methods supported are “DES Data chaining” and Triple DES.
For uploading to the server, start eCLIPse and logon to the USB token. Two of the encryption keys stored in the USB token are used to encrypt the data prior to uploading. The encryption keys, selected by head-office administration, are different from the server to laptop decryption keys. The file is encrypted and pre-pended with the indexes of the encryption keys placed in the file header. After reception by the head office, the data is decrypted in decrypted in the same way as files sent to the laptop.
All encryption keys and key locations in the table are managed with the eCLIPse administration facility. The administration facility is a head-office tool, and it is the only place where one can initiate an update to the USB token. All information on the USB token is hardware protected and encrypted. Common practice is to update all the USB tokens and decryption keys every other year.
Two different recipients with copies of the same data, after encryption, may receive differently encrypted downloads as the “table with keys” and the ordered list of encryption/decryption keys may differ from USB token to the next. This means that if one individual loses his USB token, the one he borrows from his peer may not decrypt his own data.
Three Strikes and Your Out
The hardware of the USB token is designed to support an absolute maximum of ten successive failed logon attempts after which the USB token must be returned for hardware re-initialisation. Within eCLIPse we have set the application logon threshold to three. In the event of USB token logon failure, eCLIPse provides for overrides via voice contact to head office. Standard questions from head-office are used to validate the user. Following user validation the user has twenty minutes to use a password given verbally or by email. He uses it to login to the USB token and is forced to immediately enter a new user password.
Session timeout
If the user leaves the laptop inactive for predefined time, eCLIPse can be set to block and requires a new logon. There is a keyboard lock option to handle coffee breaks.
The USB token remains on the owner’s keychain, is not stored with the laptop and is not normally interchangeable with another users USB token. Each USB token also has a logon access mechanism, with options to control number of logon attempts before lockout, number of allows executions, timeout mechanisms and many other selectable security functions.
eCLIPse provides up-to-date safe transfer of confidential data to and from managers and auditors, all the while preventing unauthorized viewing. Encryption security is managed by eCLIPse's head-office administration system, tailoring full transfer management of encrypted data between the individuals laptop and head office.
eCLIPse Modes of Operation
eCLIPse may be setup for batch download.. eCLIPse itself does not do the file transfer. Encrypted files are stored on the laptop or on a flash drive. No unencrypted data will be present on either. eCLIPse may also be used for real-time live access. Application Programming Interfaces (APIs) are provided.
Some additional system management information
USB token management. When the head office client receives his order of serial numbered USB tokens, he registers the serial numbers in a database and listed as unassigned. The database design can hold information for 10,000 USB tokens. A USB token can be used with one or more applications but to only one specific user. If need be, a user may have more then one smart-card USB token, to answer his particular needs.
Usage Examples
A large Canadian Banking-Financial Institution has regional data centers in different localities. After the head-office data processing of sensitive business data is completed, the files are encrypted and sent to their regional centers. The regional centers decrypt the received file and immediately re-encrypt it for the authorized user of the USB token. This action prevents a head-office person from knowing decryption information for the files destined to the end-user. In 10 years of use, no security loss of confidential encrypted information has ever occurred. This institution dedicated two of the 10 encryption key slots for global inter-branch transmission. A user uses the USB token to encrypt and transfer data that is needed in another branch.
Canada’s Quebec Provincial auditors, l'Autorité des marchés financiers, are using the eCLIPse system to manipulate laptop based secure data.
Not implemented is Public key encryption or PGP, but may supported on request. Triple DES is banker secure, executes well on older laptops as well proven.. The USB token keys for future algorithm support may vary from 64 bits to 640bits (8 bytes to 80 bytes).
The eCLIPse USB token is validated to security level FIPS 140-1, level 3, from the National Institute of Standards and Technology, USA.
Initialization - Setting up the keys
A standard practice is to have groups of two users from two business areas with each user only providing one half of an encryption key. The company is protected, since this practice ensures that one user does not know the other’s key choice. Putting the two halves together by random selection means that each user does not know a final key value. eCLIPse supports multiple encryption tables with randomly assigned keys. Head office security administration sets up the USB token contents to match. There are two levels of head office control. One is constructing one more tables by choosing ten keys to insert into a table, and the other is choosing which of the keys from within an assigned table will be further assigned to an individual or group. Essentially, each business area may set up its own table and assign users to specific keys.
Comparison with Hard drive Encryption
eCLIPse encryption management is the best solution. Here is why. The argument that one will provide is, why not use a hard drive that is fully encrypted, who needs eCLIPse ?
When the hard drive is encrypted, a problem may arise if a file has to be copied or if maintenance has to be performed. An encrypted copy from that hard drive may not decrypt correctly on the target device. This is usually due to hardware differences between disk drives from the same manufacturer and especially if the target drive has no encryption. If a technician has to repair the contents of the system with the encrypted hard drive, he needs the encryption / decryption keys (provided at logon). If he can log onto the system, he has access to the data, and likewise, so can a hacker. Other concerns include alpha-numeric sorting of encrypted data. There is no guarantee that in using an encrypted drive, data can be sorted in lexicographical order.
Your company’s “Information” is more valuable than the computer it is on. If your laptop computer is lost or stolen, your confidential information cannot be decrypted without your authorized USB token.
Other Uses for eCLIPse
Do you have trouble remembering all your passwords and other personal information? With eCLIPse, you can safely store them in an encrypted file protected by the USB token.
How Eclipse works
Easy, first you will receive the pre-encrypted file (s) from Head Office. The encrypted file was created choosing two of the 10 keys. Instead of transmitting the keys, the index entries of these two keys prefix the data along with other meta data, such as the encryption algorithm used. The file is sent to the user(s) using a safe file transfer method (Secure FTP in an SSH environment). Note that the 10 keys stored in the USB token are identically stored in the head office image of the token’s table.
To view the file, start eCLIPse and plug in and log-into USB token. The two key indexes and the encryption method is read from the file. The two index values are used to retrieve the decryption keys from the USB token. Along with the algorithm ID, decryption takes place. Encryption publication methods supported are “DES Data chaining” and Triple DES.
For uploading to the server, start eCLIPse and logon to the USB token. Two of the encryption keys stored in the USB token are used to encrypt the data prior to uploading. The encryption keys, selected by head-office administration, are different from the server to laptop decryption keys. The file is encrypted and pre-pended with the indexes of the encryption keys placed in the file header. After reception by the head office, the data is decrypted in decrypted in the same way as files sent to the laptop.
All encryption keys and key locations in the table are managed with the eCLIPse administration facility. The administration facility is a head-office tool, and it is the only place where one can initiate an update to the USB token. All information on the USB token is hardware protected and encrypted. Common practice is to update all the USB tokens and decryption keys every other year.
Two different recipients with copies of the same data, after encryption, may receive differently encrypted downloads as the “table with keys” and the ordered list of encryption/decryption keys may differ from USB token to the next. This means that if one individual loses his USB token, the one he borrows from his peer may not decrypt his own data.
Three Strikes and Your Out
The hardware of the USB token is designed to support an absolute maximum of ten successive failed logon attempts after which the USB token must be returned for hardware re-initialisation. Within eCLIPse we have set the application logon threshold to three. In the event of USB token logon failure, eCLIPse provides for overrides via voice contact to head office. Standard questions from head-office are used to validate the user. Following user validation the user has twenty minutes to use a password given verbally or by email. He uses it to login to the USB token and is forced to immediately enter a new user password.
Session timeout
If the user leaves the laptop inactive for predefined time, eCLIPse can be set to block and requires a new logon. There is a keyboard lock option to handle coffee breaks.
The USB token remains on the owner’s keychain, is not stored with the laptop and is not normally interchangeable with another users USB token. Each USB token also has a logon access mechanism, with options to control number of logon attempts before lockout, number of allows executions, timeout mechanisms and many other selectable security functions.
eCLIPse provides up-to-date safe transfer of confidential data to and from managers and auditors, all the while preventing unauthorized viewing. Encryption security is managed by eCLIPse's head-office administration system, tailoring full transfer management of encrypted data between the individuals laptop and head office.
eCLIPse Modes of Operation
eCLIPse may be setup for batch download.. eCLIPse itself does not do the file transfer. Encrypted files are stored on the laptop or on a flash drive. No unencrypted data will be present on either. eCLIPse may also be used for real-time live access. Application Programming Interfaces (APIs) are provided.
Some additional system management information
USB token management. When the head office client receives his order of serial numbered USB tokens, he registers the serial numbers in a database and listed as unassigned. The database design can hold information for 10,000 USB tokens. A USB token can be used with one or more applications but to only one specific user. If need be, a user may have more then one smart-card USB token, to answer his particular needs.
Usage Examples
A large Canadian Banking-Financial Institution has regional data centers in different localities. After the head-office data processing of sensitive business data is completed, the files are encrypted and sent to their regional centers. The regional centers decrypt the received file and immediately re-encrypt it for the authorized user of the USB token. This action prevents a head-office person from knowing decryption information for the files destined to the end-user. In 10 years of use, no security loss of confidential encrypted information has ever occurred. This institution dedicated two of the 10 encryption key slots for global inter-branch transmission. A user uses the USB token to encrypt and transfer data that is needed in another branch.
Canada’s Quebec Provincial auditors, l'Autorité des marchés financiers, are using the eCLIPse system to manipulate laptop based secure data.
Not implemented is Public key encryption or PGP, but may supported on request. Triple DES is banker secure, executes well on older laptops as well proven.. The USB token keys for future algorithm support may vary from 64 bits to 640bits (8 bytes to 80 bytes).
The eCLIPse USB token is validated to security level FIPS 140-1, level 3, from the National Institute of Standards and Technology, USA.
About Encrypted Security Systems
Federal Information Processing Standards Publication (FIPS PUB) 140-2, Security Requirements for Cryptographic Modules, specifies the security requirements that are to be satisfied by the cryptographic module utilized within a security system protecting sensitive information within computer and telecommunications systems (including voice systems).
The standard provides four increasing, qualitative levels of security: Level 1, Level 2, Level 3, and Level 4. These levels are intended to cover the wide range of potential applications and environments in which cryptographic modules may be employed. The security requirements cover eleven areas related to the secure design and implementation of the cryptographic module.
These areas include the following:
1. Cryptographic Module Specification
2. Cryptographic Module Ports and Interfaces
3. Roles, Services, and Authentication
4. Finite State Model
5. Physical Security
6. Operational Environment
7. Cryptographic Key Management
8.Electromagnetic Interference/Electromagnetic Compatibility (EMI/EMC)
9. Self Tests
10. Design Assurance
11. Mitigation of Other Attacks
The Cryptographic Module Validation Program (CMVP - www.nist.gov/cmvp) validates cryptographic modules to FIPS PUB 140-2 and other cryptography based standards. The CMVP is a joint effort between NIST and the Communications Security Establishment (CSE - www.cse-cst.gc.ca) of the Government of Canada. Products validated as conforming to FIPS PUB 140-2 are accepted by the Federal agencies of both countries for the protection of sensitive information (United States) or Designated information (Canada).
In the CMVP, vendors of cryptographic modules use independent, accredited testing laboratories to have their modules tested. Organizations wishing to have validations performed would contract with the laboratories for the required services.
The standard provides four increasing, qualitative levels of security: Level 1, Level 2, Level 3, and Level 4. These levels are intended to cover the wide range of potential applications and environments in which cryptographic modules may be employed. The security requirements cover eleven areas related to the secure design and implementation of the cryptographic module.
These areas include the following:
1. Cryptographic Module Specification
2. Cryptographic Module Ports and Interfaces
3. Roles, Services, and Authentication
4. Finite State Model
5. Physical Security
6. Operational Environment
7. Cryptographic Key Management
8.Electromagnetic Interference/Electromagnetic Compatibility (EMI/EMC)
9. Self Tests
10. Design Assurance
11. Mitigation of Other Attacks
The Cryptographic Module Validation Program (CMVP - www.nist.gov/cmvp) validates cryptographic modules to FIPS PUB 140-2 and other cryptography based standards. The CMVP is a joint effort between NIST and the Communications Security Establishment (CSE - www.cse-cst.gc.ca) of the Government of Canada. Products validated as conforming to FIPS PUB 140-2 are accepted by the Federal agencies of both countries for the protection of sensitive information (United States) or Designated information (Canada).
In the CMVP, vendors of cryptographic modules use independent, accredited testing laboratories to have their modules tested. Organizations wishing to have validations performed would contract with the laboratories for the required services.
Subscribe to:
Posts (Atom)
